Imagine this scenario. You have a SharePoint 2007/2010/2013 server in your environment along with an Exchange 2007/2010/2013 server. You have configured email-enabled lists in your SharePoint environment by leveraging an SMTP server configured on your SharePoint server along with a send connector on your Exchange server. Everything works great and people can email an address and have their content automatically added as a SharePoint list entry.
Then you migrate to Office 365 in a full cutover migration, obsoleting your Exchange on premises server. Your email to list functionality breaks. What now?
I found myself in this exact situation and had to come up with a solution. Here is what I came up with. I won’t be covering every step here and instead will only consider high level requirements. If you need more specific detail, please ask in the comments.
First, if you have performed a cut over migration, you likely don’t need the firewall rule you had for port 25 to your Exchange server anymore. So the first thing to do would be to modify that firewall rule and redirect traffic for it from your Exchange server to your SharePoint server.
From there, you can do the following:
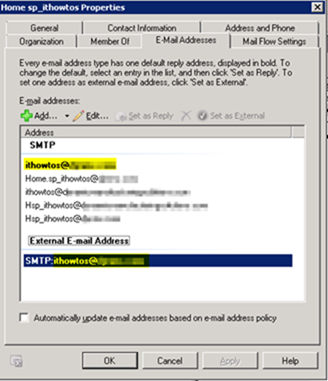
1) Modify your existing Exchange contact that is used for email to list functionality. Change the email address from [name]@sharepoint.domain.com to [name]@domain.com where domain.com matches your primary production domain.
Next, if you are using some type of Directory Synchronization tool, perform a sync to Office 365.