This HOWTO is a proof of concept to demonstrate a way to take an Active Directory environment on one server and restore it to a different server on an entirely different network. The scenario in this example is we have a domain controller which has a number of other third party applications installed and we wish to migrate just the AD portion to a new dedicated Active Directory server in a separate environment. Once completed, the old server will be permanently powered off.
We will have two systems, one called PRODDC1. This is our production system hosting Active Directory and all of our other applications. The second system is called initially NEWDC1. This is a fresh copy of Windows 2012 R2 with no configuration of any kind, not even a hostname or IP assigned. Crucially, these two systems are on isolated networks and cannot see each other.
On PRODDC1
- From Server Manager, installed the Windows Server Backup Feature
- Once installed, run Windows Server Backup and from the left menu choose Backup Once
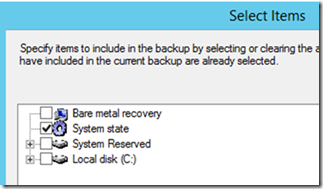
- Choose Custom and select only System State