What do you do when you need to provide a password in a batch file or to a legacy command line application but don’t want to store the password in plain text inside of the file? As usual, it’s Powershell to the rescue.
The basic steps are:
- Create a text file that contains the encrypted version of your password
- Read that password into a variable
- Convert that password into a Credential Powershell object
- Call a method of the credentials object to pull out the plain text password
The code looks like this:
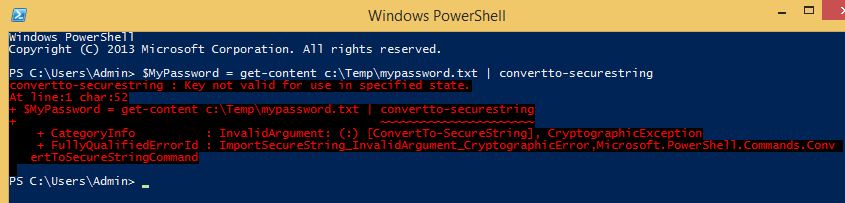
#Run one time to create the encrypted password file then remove this line Read-Host -AsSecureString | ConvertFrom-SecureString | Out-File c:\temp\cred.txt # Read in the password file you created and convert it to a securestring $password = get-content C:\temp\cred.txt | convertto-securestring # Create a Powershell Credential object that includes this password. # Note that a username is also required but my command doesn't take a username so I just filled it something. It also can't be blank $creds = New-Object System.Management.Automation.PSCredential -argumentlist "MustHaveSomething", $password # Run the legacy command and call the GetNetworkCredential method with the password property # The application will get the password but the end user will never see it. You'd have to have administrator access to the machine and a debugger to get the password &reflectverify.exe d:\Backup\* -p $creds.GetNetworkCredential().Password
So ultimately if someone has a copy of cred.txt, they can still use it to access the resource but at least this way they don’t know what the actual password was.
Update
I’ve spent a little more time with this concept and wanted to share my findings. The convertto-securestring cmdlet leverages the “DPAPI” or Data Protection API for Windows. This API creates a local key that is tied to the SID of the logged in user account as well as a master key file stored inside the users profile. What this means is that even if someone else gets a copy of your encrypted text file, they will NOT be able to use it. I confirmed this by loading up a new Windows 8.1 VM and trying to read the encrypted password I created on my source machine. It fails with the error “Key not valid for use in specified state.”
I then investigated a bunch of methods for backing up and restoring the key. I exported all of the keys in my certificate store on my source machine to the destination. I copied the master keys from the source at:
C:\Users\[UserProfile]\AppData\Roaming\Microsoft\Protect\[SID]
I used the password recovery disk and export credentials functions built in to Windows. Unfortunately (or fortunately depending on how you look at it), none of the options allowed me to run the script on the new machine.
The closest I found was this Microsoft article from 2009 that talks about exporting the DPAPI keys and making registry changes and running a command called dpaimig.exe.
http://technet.microsoft.com/en-us/library/ee681624(v=ws.10).aspx
None of this worked for me either.
Therefore the moral of the story appears to be this:
If you use the convertto-securestring functionality in a batch script or scheduled task, you need to be aware that validating those credentials is dependent on the user running the command being the same one that generated the key. So you’ll need to generate the initial key with your service account for example. Likewise, if you ever have a computer crash or need to migrate the computer, you’ll need to regenerate the password key file. Therefore it will be necessary to store the password somewhere else (Keepass for example) for documentation and disaster recovery purposes.
At the end of the day, it’s still an improvement over storing the password in plain text in the file!

10 comments
Skip to comment form
Some people then again pay a lot money at one time to lift the chance of winning.
The system where betting money is through your bank is secure to
work with, and the transaction is all the time between your account and the Ladbrokes.
Simple system described in steps. Many are simple people just struggling to get by.
This information gives all the info it’s essential get into the sport.
But the factor is that to increase your chances of successful, you want to position a wager day by day.
Instead, you’ll be able to get all the information you need from that same
site. As lengthy because the proprietor of the Bitcoin looks after
it properly utilizing a high-security wallet and two-issue authentication, it
will likely be extraordinarily tough for anybody else to
get entry to their funds. At any level, nevertheless, the bookie
can leap in and make changes to the traces that are available to his gamers if knows he will probably be getting heavy one sided
motion.
If you’re a type of individuals who doesnt like cats, Im sorry to hear that.
For the above example, it will seem like -7.5 (-110). Different
players can legally purchase Mega Thousands and thousands
Lottery tickets online via the lottery agent you see talked about above.
For instance, MEGA Hundreds of thousands is a multi-state lottery and it operates in eleven states.
As an example, you wouldn’t need to pick just any
race horse in hopes of successful a wager. 5. Guess on sports by inserting your wager.
When you click on on the sport of your selecting you should definitely bookmark the web page so
you will at all times have the most current and updated sports activities betting odds at your disposal.
In this method, you could choose a low number from the given set such as 1-50 like 1.
Some profitable numbers have two consecutive numerals, although not all the time.
After which with the time you saved do something extra
productive than you’ll have performed performing like a
poor individual.
S128 Indonesian Cockfighting Site
Wagering games that are very attached with the hearts of Indonesian individuals are known as s128 cockfight
gambling. Looking in Indonesia’s historical record, cockfighting games have existed actually
since the days associated with the dominion. This activity will be
not only entertainment but will be also a part of a
culture passed down through decades of Indonesian ancestors.
Unfortunately, although this activity is usually a
cultural heritage regarding thousands of years, the Indonesian government does not discriminate in enforcing the law until finally it is
extremely difficult to look for a spot to play cockfighting in Indonesia.
Fortunately technology invented the internet because in typically the modern era like you can now again access exciting video games through an internet relationship.
Enough using the capital regarding electronic devices like notebooks, computers or smartphones connected to the internet,
a person can immediately enjoy the excitement of playing.
Presently there are indeed many gambling online sites that provide similar gives on the internet, nevertheless unfortunately only a
few of these kinds of sites can be trustworthy. Only a handful
regarding sites have the ability to provide specialist services that
are worthy of being obtained by clients as provided by the city of S128
Sabung Poultry.
S1288 or better known as S128 has been existing for years serving every lover of online game cockfight gambling throughout Asia, even the world.
Hundreds of individuals are linked each week to be able to
enjoy every match which is presented and you could watch typically
the match directly through the available live streaming.
Right now there are many interesting characteristics that are
owned by simply s128 as the greatest chicken gambling bookie within Asia.
Listed here are interesting features that you ought to know:
Live loading!
The first advantage you will get from playing cockfighting is the availability of live buffering chicken battles that are served
in HD or perhaps high definition quality. I think very clear so that
an individual won’t miss a single bit of excitement by choosing S128 as your online gambling partner.
Various competitions are available
There are several tournaments that you take component in at all times so zero need
to be scared you may not get a online game because
with s128 poultry matches will always be present each day and you will enjoy the variety of games you need.
Attractive Bonuses and Special offers
Customer comfort is a new top priority for us.
Therefore, this site has offered many interesting bonuses plus promos
that you can follow as an official member. These bonuses and promos are given since thanks
from s128 to be able to customers for choosing all of them as partners
to play online gambling.
How to be able to Play Chicken Gambling on S128
All you want to do first just before starting the game is to register yourself as a member on the Betberry
site. It’s easy, visit the official Betberry website
and your registration menu. Complete the enrollment process and you can immediately
get a user ID and password that you will later
use to sign into the game.
Exploring every online gambling game on the internet has become one of the undertakings most enjoyed by users of gambling facilities nowadays.
How not, every the games that used to be abandoned enjoyed abroad by people
from the upper classes, now you can enjoy without having
to depart the house and use a more affordable cost to fake slot gambling in the house.
This is all thanks to internet technology that can border online gambling fans behind the
best gambling bolster providers on the world. As in Indonesia itself, the
recognized online gambling agent site behind Depoxito is here to
abet those of you who desire to spend release times following feel online gambling products.
Since its presence in the domestic online gambling industry, Depoxito has
presented various types of gambling games of the highest quality.
Games such as soccer betting, casino, shooting fish, poker,
lottery, and of course online slot games are affable subsequently
international standards because they arrive from leading gambling sites such as Sbobet, Spade Gaming, Microgaming, Playtech, and as
a result on.
For those of you who want to attempt out how carefree it is to ham it up online gambling upon the certified gambling agent website Depoxito, hastily register
now and enjoy the best online gambling experience that you can’t locate anywhere else.
Depobola is one of Indonesia’s most significant
online soccer wagering sites today. And exactly why is
it necessary to choose Depobola because your partner?, because Depobola is one of the particular agents that has a great official license and is also signed up as a
trusted company at the center, Depobola is also here as an agency that may
be believed to have a complete game.
Depobola is also one of the Trusted Gambling Agents, inside addition we here offer
the best service from all experienced customer services professionals who will directly serve you, besides that here we keep typically
the safety and comfort regarding members
in playing on our website, Depobola’s website is usually wrong one website that often holds interesting events in addition to promotions that are
very necessary for our loyal members, obviously.
To become Indonesia’s greatest soccer dealer, is an online gambling site that already
has licenses plus licenses as well since being an online gambling web site that provides
the very best services.
The Advantages of Depobola With Other Sites
The established online gambling game that we provide
here is usually Sportbook, Sportbook is 1 of the online betting related to sports,
plus Depobola here provides IDENTIFICATION with the best market, besides Sportbook here we also provide Livecasino, Slots, Joker123 Seafood Shoot,
S128 Cockfights, Togel Chicken Singapore,
Hongkong Togel, Kuala Lumpur Togel, carry out not hesitate to join up and get an account
coming from Depobola, to Register Depobola is very easy
and the particular security of your data is maintained
with the security system that may be certain.
Here we provide products which have guaranteed safety, the items we provide are SBOBET, MAXBET (IBCBET).
Both associated with these products have already been tested from immunity towards cyber crime,
phishing, ripoffs, and fraud, besides that Depobola is also a single of the biggest on-line gamblers in Asia.
Apart from friendly professional consumer service, here you will additionally be given a very quickly deposit and withdrawal
method, not later than 5 minutes.
Depobola also offers backup data where an individual can login Depobola with the website
that we supply, it avoids the wrong use of data and maintains the particular security of information members.
To conduct transactions, here Depobola provides complete banks such as BCA, BNI, Mandiri, BRI, CIMB, and
then for dealings here Depobola serves 24/7.
And here Depobola likewise gives access to users who join our web site to see the assertions who have been successfully gamble, besides members who have joined our
website may also get the chance to take part in typically the sportbook tournament that all of us have for free, the particular sportbook tournament is a single of the facilities that will Depobola provides
to Depobola loyal members.
Depobola Alternative Links
To make that easier for players to be able to play soccer gambling
on the smartphone, the football betting agent also provides the link that can be accessed anytime and everywhere of
course with the availability of an alternative depobola link.
Considering that right now there is of positive internet in Indonesia, the particular provider always
provides up to date alternative links in order to smooth the members
to the original web site. In addition to the positive internet right now there are also a number
of other football agents sometimes ignorant upon behalf
of the depobola alternative site. So that makes us always advise that loyal
members must really ensure that the website they visit is depobola.
The very best and Most Trusted On the internet Sbobet Agent
Playing about online gambling sites has become a familiar thing with regard to fans of this online game to use their luck.
Specially in a country that forbids all varieties of gambling activities such as Indonesia,
Sbobet agents are increasingly mushrooming and are becoming a
new popular alternative for bettors to channel their hobbies safely.
In modern occasions, bettors no longer require far to Las Vegas or Macau to look for bookies.
Only with a home computer or laptop, even more simple, smartphone
and internet network, whoever and wherever you are, can immediately perform
online gambling comfortably and freely.
Indeed, finding the trusted Sbobet agent in order to
be used as a play partner is a challenging problem. With so several sites offering a variety of attractive features and promos, it’s difficult in order to
distinguish which kinds actually provide professional services
in addition to which types are phony.
Most people will choose the biggest gambling site straight that
may be chosen by the bettor, however the drawback is
generally required a large deposit to be able to register / join the particular
game. Even some individuals, you can find those who locate it difficult if
you have to use sites that use English.
Finally, the players, especially in Indonesia, inevitably
have to be able to find an Indonesian gambling online agent who certainly provides international quality games and is
also able to provide the particular best service but however provides comfort in playing plus will not make a busted wallet.
Tips for Selecting a Trusted Soccer Gambling Real
estate agent
There are several large names online that you can decide on as play partners.
Between Depobola. This agent is usually arguably the biggest betting promoter in Indonesia who has served its people for years.
Listed below are the particular reasons why Depobola is very popular as a reliable Sbobet Indonesia agent.
day to day Customer Support
The very first feature you must have is having CS or perhaps Customer Support that is usually always online at just about all times.
This is intended in order that the comfort plus overall flexibility of members when playing always awake.
Any kind of difficulties and confusion faced by players can become immediately
resolved with the aid of Consumer Support who can always be
contacted for twenty four hours straight. And stay away
from agents whose customer support is difficult to contact, that could be that the
particular site is fraudulent.
Safe & Fast Financial Dealings
Not all trusted soccer gambling agents possess a great financial transaction system.
Several of them require very a long time, also up to days
plus cannot guarantee the safety of their customers when transacting.
Unlike the truth together with Depobola. Financial transactions this kind of as deposits, withdrawals, and
transfers can be carried out in just minutes in addition to of course use
a high-level security system. In inclusion, the process can be carried out
easily because it has worked closely with various major banks inside the
country.
Several types of Online games
If in the previous gambling only struggled close
to lottery and soccer gambling, now Depobola provides thrilling innovations by presenting a
new variety of interesting plus fun games. Not simply being an agent
of Sgd777 Online, variations of cards games for example poker or even dominoes, casino games such as roulette or baccarat, to the slots provided.
All game products usually are sure to have grade-A
quality since they are provided by major gaming providers such because Sbobet,
Maxbet as well as others. Simply at Depobola, internet gambling provides the most complete online game by
ensuring you can spend time without feeling uninterested.
Attractive Promos and Bonus deals
The last tip for choosing the best site is usually to ensure that the
site offers a sizable selection regarding promos and bonuses that are a shame in case you miss them.
This function will make the online game easier and more fun.
Depobola has prepared various advertisements and bonuses that can be obtained by members in a simple way.
For example , like a welcome added bonus promo, to only require to register as a member, then you certainly automatically have got the right to be capable of getting the bonus.
There usually are still many other promos provided by the best Depobola agents.
Therefore, don’t wait any kind of longer and immediately sign up yourself now to sign up for with millions of other users to feel the exhilaration of playing with Reliable Online Sbobet agents within Indonesia.
If you are playing online slots using genuine child maintenance for sure, you should pay
attention to some of this past you finally fail to bring house the victory.
In this unbiased time you can be active online slots something
like everywhere, even to create transactions you can furthermore use online bank transfers or even upon some sites you can create deposits using credit.
Some things that you have to pay attention to
are actually quite common, but people often ignore them and
underestimate them, therefore in the stop what happens is that the person loses every of the initial
capital to bet. fittingly you should begin reading
again and listening to some of the subsequent
to that will create you skilled to enjoy online
slot games without heartbreaking roughly losing.
Hmm is anyone else encountering problems with the images on this blog loading?
I’m trying to determine iff its a problem on my endd or if
it’sthe blog. Any suggestions would be greatly appreciated.
Gratis forex grafiek africa-option.com geen deposito binêre opsies nie
The best in class, Depoxito find the money for you high-end experience that adopt the look and
environment of authentic VIP standarts, we present you the best glamorous
to high-level experience of VIPs expect in any summit stop casino, grand bring to
life casino royale find the money for you the new studio design element including the
grand blackjack, offering our VIP Customer the best experience of a Salon privee table.
New style table afterward feature across the room gone grand roulette
upgraded upon our provider playtechs mini prestige roulette which delivering more
engaging and richer playing experience. The extra experience contains a sum of seven tables including five
blackjack tables, one roulette table and one baccarat table.
Grand living casino royale has been tall hand-engineered to fit the needs of our customer to using it, and contains unique elements that is specially meant to maximize the impact
value we got from our customers and diversify it to the existing network.
Soon, Depoxito will build an augmented certainty technology
upon alive casino for our VIP member, these most broadminded technology ever seen in stimulate casino including this greater than before reality.
Which permit players to experience products on an entire extra level which is never seen in the
past literally leaping out of the game and taking the blackjack,
baccarat, roulette and other game into the collective entire level.
Depoxito VIP Baccarat, we allow you the certainly
exclusive live VIP Baccarat that is played subsequent to
going on to 7 players at the similar table and our severely trained beautiful
alive baccarat dealer. And of course our VIP believer will setting as if they
were truly sitting at one of the summit casino baccarat table.
This immersive gaming experience creates a hugely
carefree tone that our VIP players will locate difficult to surpass.
Here is the list of enliven casino game that depoxito provide, we come up with the money for the widest range of breathing casino games on the shout from the rooftops
including : blackjack unlimited, blackjack prestige, roulette, baccarat, poker,
hi-lo, sic bo, and grand stimulate casino royale such as Grand Baccarat, Grand Blackjack and Grand Roulette
for our VIP member. And of course as a enthusiast of Depoxito you can enjoy
every the games that we have enough money to you, all you habit to reach is just
visit our site depoxito and register it lonesome takes up to 3 minutes and then youre suitable to deed any game that you want.
Be our VIP, physical our VIP believer of course contracted you the best
abet you can get from us every you need to be
a VIP member is entirely easy. all you infatuation is just keep playing upon our
site, lump and action later a VIP past the amount that our company had written, save playing and our customer promote will gain access to you
that you are promoted to become a VIP enthusiast upon our site.
Alternative Links to Established Online Gambling Sites
Now in an all-sophisticated era, everyone can access the internet
very easily. So far many online games that may be
performed by everyone, one example is online gambling games.
With the appointment of wagering that used to be only on land, now an online system has made
it very easy for many betting players to route their hobbies in the world of
gambling online.
asianbokie88 website prediksi skor bola https://asianbookie88.com Thank you for the info.